Blog roll please!
Quick reads across a variety of topics
Vitalik Buterin At Radicalxchange Taipei On Harberger Taxes
Blockchain
18 Jul
00:40

On Tuesday (7/16), Vitalik Buterin, the creator of Ethereum, gave a 30-minute presentation entitled, “Harberger taxes for virtual property.” In his presentation (18 slides in English and Mandarin) at the first event of RadicalxChange Taipei, Vitalik looked at what Harberger taxes are and what are the ways to apply Harberger taxes for domain names. Vitalik’s presentation starts at 1:50:47 in the YouTube video. Diode, a developer of blockchains for IoT devices, believes in the vision...
Hardware Requirements Of Blockchain Clients
IoT
15 Jul
11:06

You just decided to start your next project using blockchain. That is awesome congrats! But now you face the many choices: Which blockchain platform and clients are technically suited for your use case? Makers and IoT specialists know that when designing embedded systems it’s important to understand the technical parameters within which each component can work. The same is true when selecting the blockchain technology. Required storage capacity on the device, RAM usage, and bandwidth...
Blockquick Reputation System
Blockquick
08 Jul
18:06

China social credit system: the method to reward or punish citizens for their behavior is unclear First announced in 2014, the Chinese government has been implementing a controversial social credit system. The system uses secret algorithms to evaluate the behavior of Chinese citizens, monitor their banking and social media information such as communications on popular chat app WeChat, violation of traffic rules, and countless other factors and criteria that the government is reluctant to publicly...
Blockquick Consensus Reputation Table Explained
Blockquick
01 Jul
14:35
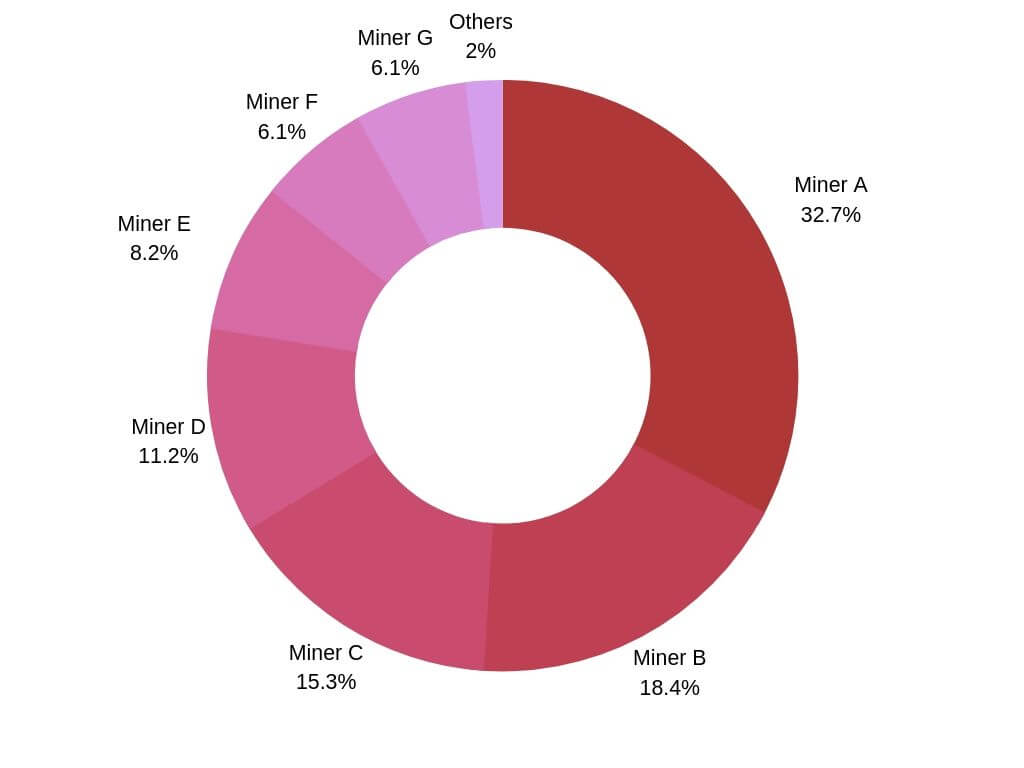
Download full paper here (PDF). Diode’s CTO Dominic Letz published a paper recently to give an introduction of BlockQuick, a super light client protocol for blockchain validation on constrained devices. One of the key concepts behind the newly proposed BlockQuick is that it plans to adopt a consensus-based reputation scheme to accept blocks. This article explores how blockchain synchronization of Internet-of-Things (IoT) devices can be achieved through BlockQuick consensus reputation table, as well as sheds...
Why The Internet Infrastructure Is Vulnerable To Bgp Hijacking Attacks
Security
24 Jun
10:02

Earlier this month, Doug Madory, Oracle’s director of internet analysis, wrote in a blog post detailing a BGP route leak incident happened on Thursday, June 6. For approximately two hours, a massive amount of European Internet traffic was rerouted through China Telecom’s own servers. The Internet traffic was rerouted following a BGP route leak at Swiss data center colocation company Safe Host. Over 70,000 routes - comprising an estimated 368 millions IP addresses coming out...
Messaging Service Telegram Was Hit By a DDoS Attack, What Needs to Change?
Security
18 Jun
16:07

According to a report, Telegram’s CEO Pavel Durov confirmed on Wednesday (June 12) that his popular messaging service experienced a “powerful” Distributed Denial-of-Service (DDoS) attack. The DDoS attack disrupted Telegram’s services for about an hour. He later tweeted that the IP addresses involved in the attack were coming mostly from China. “IP addresses coming mostly from China. Historically, all state actor-sized DDoS (200-400 Gb/s of junk) we experienced coincided in time with protests in Hong...
Proof Of Stakework A Community Vision
Blockchain
17 Jun
17:46

[Note: This post is a follow-on discussion to topics discussed in Introducing Proof-Of-StakeWork and requires some background knowledge in blockchain technology.] In the last post on Proof-Of-StakeWork we talked about some of the advantages and disadvantages of both Proof-Of-Work (POW) and Proof-Of-Stake (POS) so I won’t go into those details here. The purpose of this post is to more fully articulate the vision and motivation behind Proof-Of-StakeWork (POSW) and to provide a little more detail...
How Blockquick Super Light Client Protocol Can Help Mitigate Eclipse Attacks
Blockchain
10 Jun
14:24

In May, Diode’s CTO Dominic Letz published a paper introducing BlockQuick, a super light client protocol for blockchain validation on constrained devices. The paper shows that unlike other existing approaches such as proofs of proof-of-work (PoPoW) and FlyClient, Diode’s BlockQuick super light client protocol is capable of protecting against eclipse attacks and man-in-the-middle attacks on a peer-to-peer network. But what is an eclipse attack? Is it possible to prevent some of blockchain’s biggest security threats?...
How Decentralized Public Key Infrastructure Will Be The Future For The Web
PKI
28 May
15:54

If you’ve been following our blog, you will have heard us mentioning the term decentralized public key infrastructure before. But you probably don’t know what it is or how it works, let alone why it matters so much. In this post, we will examine current approaches to the traditional centralized PKI, explore the basics of decentralized public key infrastructure (DPKI), and then show how blockchain-based DPKI can make an impact as the industry transitions to...
Blockquick Super Light Blockchain Client For Trustless Time
Burning Platform
24 May
19:12

- Click here if you just want to read the Paper - In the last two posts of this series, we first introduced the governance issues in PKI and then the circular dependency between establishing trust in PKI certificates and establishing the current time on a connected device. So let’s break that circular dependency between time and trust. The difference between trusting a person/an entity and trusting data is key here. How can we establish...
